ドメインハイジャックに対処する方法:解決策とベストプラクティスを含む詳細なチュートリアル

ドメインの乗っ取りは、ウェブサイトの評判とセキュリティを損なう可能性のある重大な問題です。自分のドメインを開いてみたら、他人のウェブサイトだった......。このシナリオは、DNS設定の侵害、サーバーの侵害、あるいはユーザーのコンピューターでのマルウェア感染など、さまざまな理由で発生する可能性があるドメインハイジャックを指していることがよくあります。DevOpsエンジニアやシステム管理者として、ドメインハイジャックのトラブルシューティングと解決方法を理解することは、デジタル資産を保護する上で非常に重要です。このガイドでは、ドメインハイジャックの原因を探り、実行可能な解決策を提供し、将来のインシデントからドメインを保護するための予防策を提案します。
ドメイン・ハイジャックの原因の理解
ドメインの乗っ取りは、一般的に3つの主要なカテゴリに分類されます:
1:DNSハイジャック
DNSハイジャッキングは、攻撃者がドメインのDNSレコードを制御し、Webサイトの訪問者を不正なIPアドレスにリダイレクトすることで発生します。これは、DNSサーバーを侵害する、ソーシャルエンジニアリングを使用してDNS管理コンソールにアクセスする、またはレジストラのインフラストラクチャの脆弱性を悪用するなど、さまざまな手段で実現できます。
- 例:一般的なDNSプロバイダを利用している企業では、攻撃者が管理するIPアドレスを指すようにDNSレコードが変更されている可能性があります。この結果、ユーザーは正規のサイトと同じように見えるフィッシングサイトにリダイレクトされることがよくあります。

2:サーバーの妥協
攻撃者がウェブサイトのファイルを変更したり、悪意のあるコードを注入したり、設定を変更してユーザーを別の場所にリダイレクトさせたりすることで、サーバー自体が侵害されることがあります。これは、ソフトウェアの脆弱性が悪用されたり、サーバーを保護するために脆弱なパスワードが使用されたりした場合によく見られます。
- 例:攻撃者は、既知のセキュリティ欠陥がある古いバージョンのCMS(WordPressなど)を介して、ウェブサーバーにアクセスします。侵入後、.htaccessファイルを変更し、すべてのトラフィックを別のドメインにリダイレクトします。
3:マルウェア感染
サーバーやDNSではなく、クライアント側に問題がある場合もあります。あなたのサイトにアクセスしようとするユーザーが、ブラウザのDNS設定をハイジャックするマルウェアに感染し、意図しないウェブサイトにリダイレクトされている可能性があります。
- 例:ユーザーのデバイスがマルウェアに感染し、ホストのファイルやDNS設定が変更されます。ユーザーがお客様のドメインにアクセスしようとすると、代わりに悪意のあるサイトに移動します。

ドメインハイジャックを解決するためのソリューション
DNSハイジャックの解決
ドメインがDNSハイジャックの被害に遭った場合は、迅速な対応が不可欠です:
ステップ1: DNSレコードの確認
などのコマンドラインツールを使用します。 エヌエスルックアップ または 掘る をクリックして、ドメインのDNSレコードが変更されていないかどうかを確認してください:
nslookup yourdomain.com
dig yourdomain.com返されたIPアドレスが正しいことを確認してください。IPが見慣れないものであったり、別の場所を指している場合は、DNS設定が乗っ取られている可能性があります。
ステップ2:DNSプロバイダーの変更
現在ご利用のDNSプロバイダーが不正アクセスを受けている場合は、より安全なDNSプロバイダーへの変更をご検討ください。以下のようなプロバイダーがあります。 クラウドフレア または グーグルDNS は、強化されたセキュリティ機能とDNSベースの攻撃に対する耐性を提供します。
例:DNSSECをサポートしていないDNSプロバイダーを使用していた場合、DNSSECを提供し、レート制限やDDoS保護などのセキュリティ機能を統合しているCloudflareへの移行を検討することができます。
ステップ3:DNSアカウントの保護
DNS管理アカウントにログインし、以下の手順に従ってください:
- 二要素認証(2FA)の有効化:これは、権限のない人がアクセスできないようにします。
- DNSSECの有効化:DNSSEC(Domain Name System Security Extensions)は、DNSレコードに電子署名を付与することで、DNSレコードのなりすましを防止します。
- 口座活動の確認:アカウントのアクティビティログを確認し、不正なログインや変更を特定してください。不審なアクティビティが検出された場合は、直ちにパスワードを更新してください。

ステップ4:DNSキャッシュのクリア
不正なDNS情報がローカルにキャッシュされないようにするには、ローカルのDNSキャッシュをクリアし、影響を受けるユーザーにも同じことをするよう促してください:
# Windows
ipconfig /flushdns
# macOS
sudo dscacheutil -flushcache; sudo killall -HUP mDNSResponder
# Linux
sudo systemctl restart nscd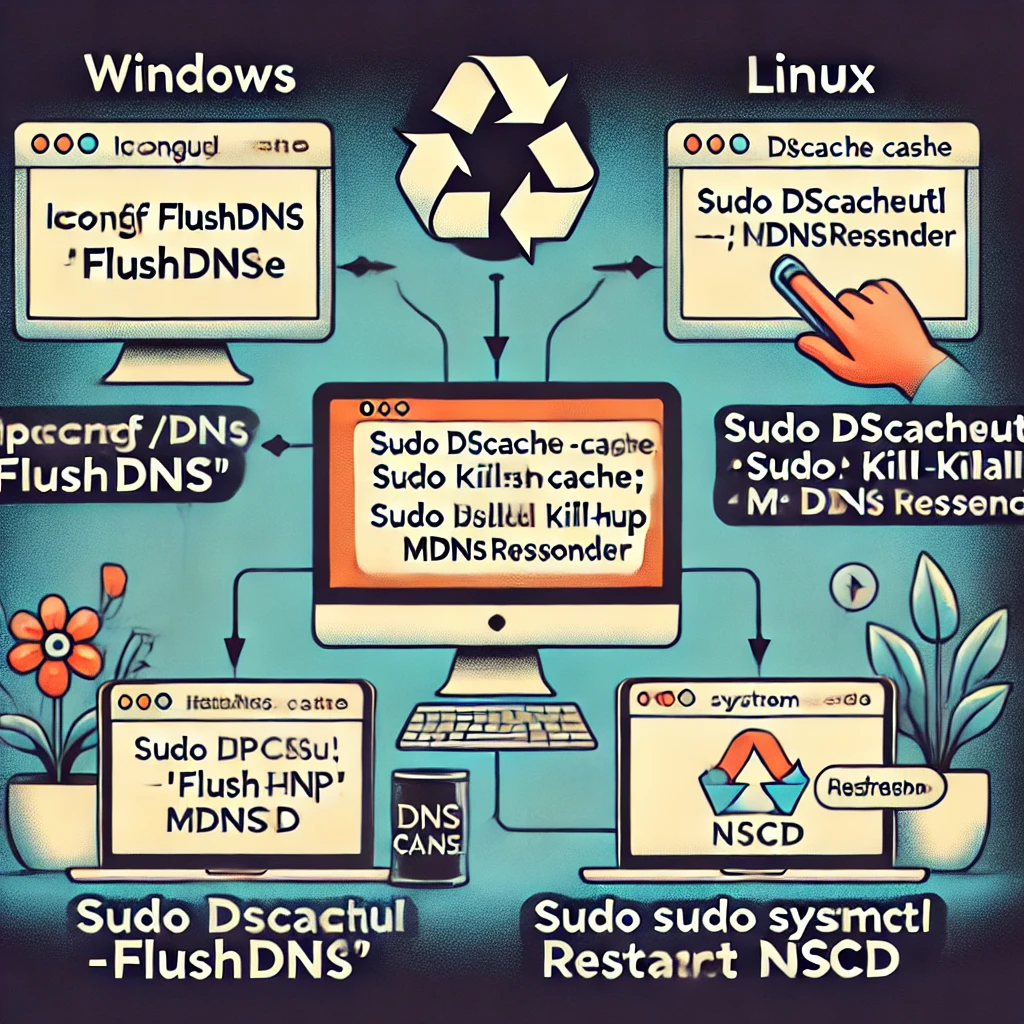
ステップ5:DNSの変更を監視
DNSレコードの変更の監視とアラートを設定します。以下のようなツールがあります。 DNSスパイ または ページャーデューティ 不正な変更が検出された場合は、通知することができます。

サーバーの危殆化への対応
DNSの設定が正しいにもかかわらず、ドメインが正しくリダイレクトされない場合、サーバーが侵害されている可能性があります。
ステップ1:サーバーファイルの復元
以下のような重要なウェブサイトファイルを調べます。 .htaccess, index.phpおよび設定ファイルが変更されていないかどうかを確認します。これらのファイルをバックアップ・バージョンと比較するには 差分:
# 現在のバージョンとバックアップを比較します。
sudo diff /var/www/html/index.php /backup/index.php不一致が見つかった場合は、変更したファイルをバックアップからクリーンなバージョンに置き換えます。
ステップ2:サーバーログの分析
サーバーのアクセスログとエラーログに異常がないか確認します:
tail -n 50 /var/log/nginx/access.log
grep "POST" /var/log/nginx/access.log # 異常なPOSTリクエストを探す異常なアクセスパターンやコマンドの実行を試みるIPアドレスを探します。

ステップ3:パスワードとキーの変更
SSHキーやデータベース認証情報など、サーバーに関連するすべてのパスワードを変更してください。強固で一意であることを確認してください。
ステップ4:サーバーのセキュリティ強化
- SSHキー認証:パスワードベースのSSHアクセスを無効にし、代わりにキーベースの認証を使用します。
- ウェブアプリケーションファイアウォール(WAF):のようなWAFを導入します。 モッドセキュリティ または クラウドフレアWAF を使用して、悪意のあるリクエストがサーバーに到達する前にフィルタリングします。
- 最小特権原則:サーバー上のファイルとフォルダーのパーミッションが、通常の操作に必要な最小限の権限に設定されていることを確認してください(例えば、PHPファイルはWebサーバーから書き込み可能であってはなりません)。
ステップ5:マルウェアのスキャン
以下のようなセキュリティツールを実行します。 アークハンター, チェックルートキットのようなサードパーティツールもあります。 スクリ サーバー上のルートキットやマルウェアを検出します。
クライアント側マルウェアの軽減
あなたの側ではすべて安全であるにもかかわらず、ユーザーがリダイレクトされ続ける場合は、デバイス上のマルウェアが原因である可能性があります。
ステップ 1: ユーザーの教育
以下のような信頼できるウイルス対策ツールでデバイスをスキャンする手順を含め、クライアント側のマルウェアの可能性について説明する通知をウェブサイトに掲載します。 マルウェアバイト または カスペルスキー.
ステップ2:ブラウザとキャッシュの設定
マルウェアはリダイレクトを継続するために保存データを操作することがよくあるため、ブラウザのキャッシュとクッキーをクリアするようユーザーにアドバイスしてください。
ステップ 3: システムの完全スキャンを提案
以下のようなソフトウェアを使用して、システムのマルウェアを完全にスキャンすることをお勧めします。 ビットディフェンダー または ノートンセキュリティ.

予防策とベストプラクティス
1.定期的なバックアップ:DNS設定、サーバーファイル、データベースをバックアップします。バックアップは、以下のような安全なストレージにオフサイトで保存します。 AWS S3 または Azure Blobストレージ.
2.セキュリティ監査:DNS設定、サーバー設定、アクセスログの定期的なセキュリティ監査をスケジュールし、脆弱性や不正変更の兆候を早期に検出します。
3.自動アラート:DNSレコードの変更、予期せぬサーバーへのアクセス、ログイン試行などの自動アラートを設定します。こんなサービス クラウドフレア リアルタイムのモニタリングとアラートを提供します。
4.コンテンツ・デリバリー・ネットワーク(CDN)の利用:のようなCDNを導入します。 アカマイ または クラウドフレア DDoS保護やリクエストフィルタリングなどの機能により、セキュリティのレイヤーを追加します。
5.ドメインロック:有効 ドメインロック レジストラを経由して、不正なドメイン転送を防止します。これにより、レジストラレベルの不正な変更に対する保護レイヤーが追加されます。
結論
ドメインのハイジャックは、トラフィックの損失からブランドへのダメージに至るまで、重大なリスクをもたらします。DNSハイジャック、サーバーの侵害、クライアント側のマルウェアなど、根本的な原因を理解することで、これらのリスクを軽減するための的を絞った対策を講じることができます。推奨されるソリューションを採用してコントロールを取り戻し、ベストプラクティスを採用して将来の攻撃からドメインを守りましょう。
強固なセキュリティ対策を実施し、警戒を怠らないことで、ウェブサイトの安全性とアクセス性を確保することができます。デジタル資産の保護に関するご質問やサポートが必要な場合は、コメント欄またはサポートチームまでお気軽にお問い合わせください。







回答